Per-policy webhooks
Castle has supported webhooks for quite some time now, as a way of automating your fraud and abuse operations. We're happy to launch a much improved version of setting up webhooks and how they trigger. In the past Castle sent out webhooks based on two static policy conditions: one for when the policy action was challenge and one for when it was deny.
Now we've introduced the "Integrations" tab for both Policies and Lists, where you can create and manage webhook triggers. One big change compared to before is that you can attach a webhook directly to a specific policy when it matches. This is useful for example when you have one specific policy for Account Sharing and one for Bot Registration. In this case you can choose to send webhooks to two different endpoints/systems depending on which Policy that match.
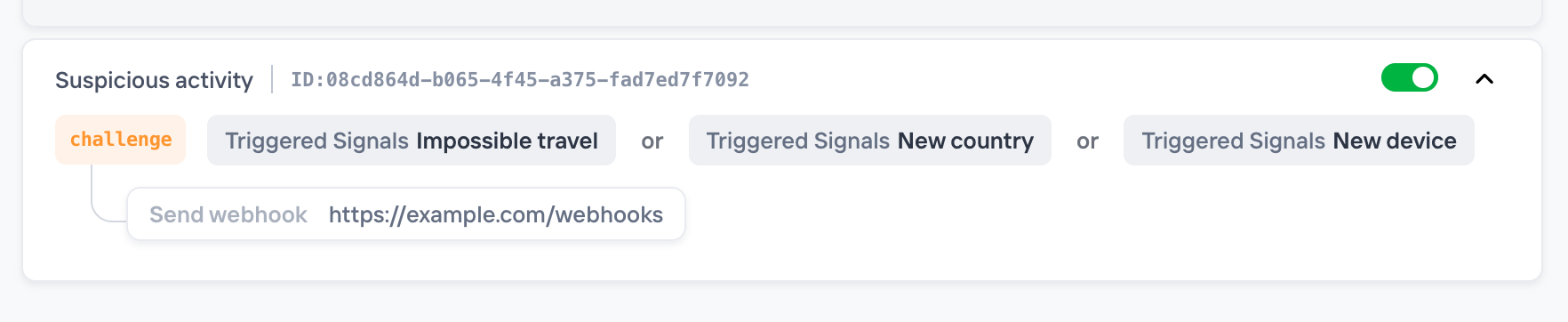
You can now attach a webhook directly to a Policy
We've also updated the payload included in the webhooks dispatched when a Policy matches, so that is fully aligns with the event information you can see in the Explore view. Check out the documentation for a complete example