Bot detection
Castle provides a comprehensive bot detection system designed to protect your platform from the growing threats of modern automated attacks such as account takeovers, fake signups, and other bot-driven threats such as spam or transaction fraud. Unlike traditional fraud prevention solutions that rely on fragmented data and siloed approaches, Castle offers a unified, holistic platform that integrates seamlessly across the entire user journey, providing unparalleled accuracy and actionable insights.
The different bot threats
Attackers are increasingly using bots to exploit business logic and gain unauthorized access to user accounts. Common types of bot attacks that Castle's system is designed to combat include:
- Credential stuffing and account takeovers. Attackers deploy bots to rapidly iterate through combinations of usernames and passwords until they find valid credentials, enabling them to take control of multiple accounts, particularly those with weak security.
- Fake and mass signups. Bots can generate large volumes of fake user accounts using fabricated information. These accounts may be used for spamming, exploiting promotions, or carrying out other malicious activities.
- In-app fraud & abuse. In-app bot attacks can take various forms, such as spamming content, spreading malicious links, or manipulating in-app features for fraudulent gain. Bots might flood chat systems with unsolicited messages, artificially inflate engagement metrics, or exploit in-app purchases and reward systems.
Bot and fraud detection in one place
Castle stands out by providing a unified approach to bot detection and fraud prevention, integrating these capabilities across the entire user journey. From the moment anonymous traffic hits your platform to in-app user interactions, Castle's system continuously analyzes both bot and human behavior to detect malicious activity early and accurately.
- Holistic detection. By seamlessly combining bot detection with behavioral analysis, Castle offers a comprehensive view of the user journey. This allows for the early identification of not just bot-driven threats but also suspicious human behaviors that could indicate potential fraud or account takeovers.
- Detecting human-driven fraud. In addition to automated threats, Castle is also adept at detecting human-driven fraud and abuse conducted at scale, such as human click farms. These operations, often organized to manipulate engagement metrics or execute fraudulent activities, can be just as damaging as bot attacks. Castle’s advanced analytics identify the patterns and anomalies typical of such human-driven schemes, providing a robust defense against both automated and human-perpetrated fraud.
- Behavioral intelligence. Traditional fraud prevention tools often focus on identity verification and transactional data, which can be easily manipulated by sophisticated bots and AI-driven attacks. Castle goes beyond these signals by leveraging advanced behavioral analytics. This approach helps Castle understand the unique patterns and nuances of legitimate user behavior, providing a more accurate assessment of risk and enabling the detection of even the most sophisticated fraud attempts.
Detection methods
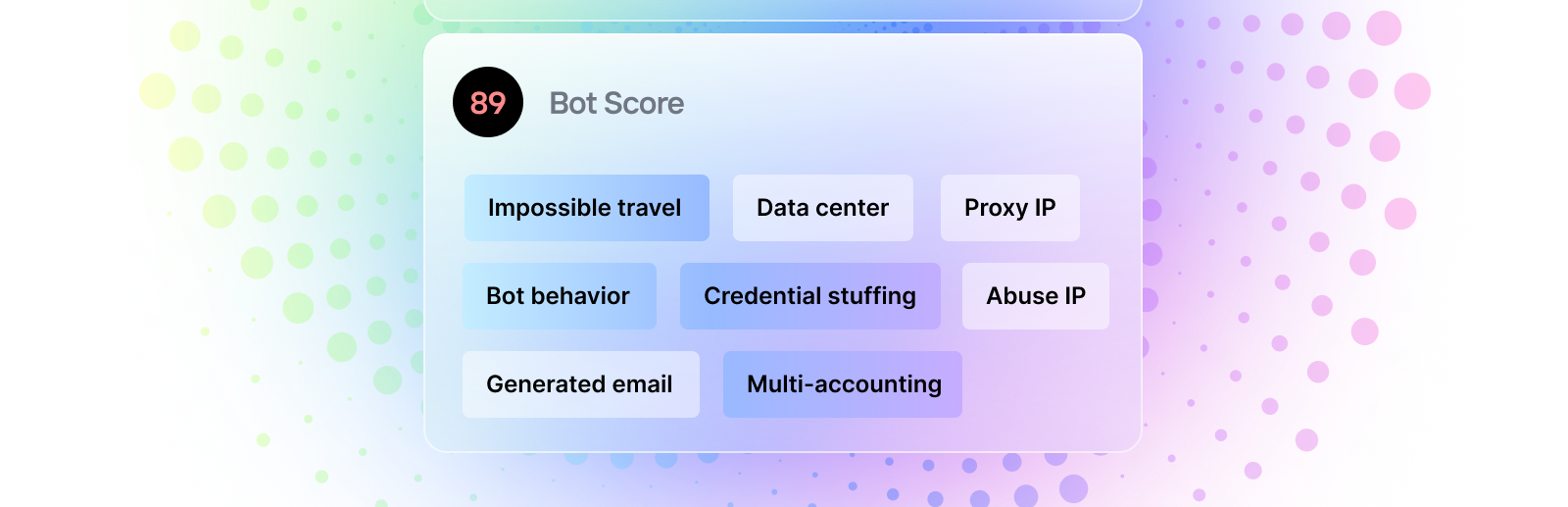
Traditional CDN based bot detection typically only rely on simple detections like HTTP headers and IP. Castle's bot detection system uses a vast combination of factors to calculate a bot score, which is central to determining the likelihood of automated activity. Key components include:
- Interaction analysis. Castle monitors mouse movements, keystrokes, and interaction patterns, in an anonymous way, to detect automation. Bots often display repetitive, unnatural behaviors, such as moving the mouse in a perfectly straight line or executing identical requests in high volumes. In the blog post Bot or Not, you can read about our approach to interaction analysis.
- Headless browser detection. Castle uses state-of-the-art techniques for detecting modern headless browsers, which are commonly used by bots. This includes detecting inconsistencies in device properties and probing for spoofed environments.
- Behavioral anomalies. Castle detects anomalies like unusual login success-to-failure ratios, sudden spikes in activity, and repetitive interaction patterns, all of which are indicative of bot behavior.
- Proxy and IP analysis. Bots often use proxies or datacenter IPs to disguise their origin. Castle flags suspicious IPs and identifies traffic from spoofed or emulated devices.
- Email analysis. Castle includes advanced email pattern analysis to detect attackers creating multiple accounts using slight variations of the same email address in a short time. It recognizes patterns like adding "+1" or altering dots (e.g., [email protected] vs. [email protected]) and groups these variations to identify likely fraudulent activity. Additionally, Castle evaluates the age of the email domain, flagging new or suspicious domains as potential indicators of bot-driven fraud.
- Javascript execution and request replays. Castle verifies Javascript execution, a key indicator of legitimate browsing, and detects attempts to bypass Javascript or replay identical requests—common tactics used by bots.
Bot scoring and risk mitigation
The Castle bot score quantifies the likelihood that a request originates from a bot, allowing you to tailor your response based on the level of risk. Common strategies for mitigation includes:
- Blocking high-risk requests. For requests with a bot score of 90 or above, it's advisable to block the request and display a non-specific error message, such as "Please use a different email address," to avoid revealing that the block is due to suspected bot activity.
- Triggering adaptive UI challenges. For requests with a bot score between 60 and 90, instead of relying on CAPTCHAs—which can be bypassed by services like 2captcha and Capsolver—we recommend implementing adaptive UI challenges that are more difficult for bots to solve. These challenges can include actions like multi-step verification processes, requiring additional user input, or presenting dynamic forms that change based on user interactions. By leveraging these adaptive techniques, you can maintain security without heavily impacting legitimate user experience.
- Monitoring and adjusting. Before deploying blocking mechanisms or adaptive UI challenges, use the Explore view in the Castle dashboard to visualize bot activity over time. This analysis helps fine-tune your settings, ensuring that you strike the right balance between security and user experience while minimizing disruption to legitimate users.
Unified investigations and response
Castle consolidates security, fraud prevention, and trust & safety investigations into a single, intuitive platform. This unified view of user activity and risk empowers your teams to make faster, more informed decisions. Our powerful rules engine allows for the automation of responses based on bot scores, user behavior, and custom policies, ensuring swift and effective action against fraudulent activities.
Implementation
Castle offers flexibility to integrate bot detection into your existing infrastructure in your preferred way:
- Filter API. The Filter API allows you to block bot traffic before it reaches your authentication logic. It can be deployed outside your app, such as within your CDN, making it a powerful tool for early-stage bot detection.
- Risk API. The Risk API is designed for in-app use, allowing you to check the bot score for authenticated users and take appropriate action based on the assessed risk.
- CDN/Edge and in-app deployment. For maximum protection, we recommend a layered approach that deploys Castle both at the edge (via the Filter API) and within your application (via the Risk API). This strategy filters out bot traffic early while providing additional scrutiny for requests that reach your application. See the CDN integration guide for more info.
Customization
Castle provides you with the flexibility to tailor detection rules, risk thresholds, and workflows to meet your specific needs. This customization ensures that Castle seamlessly adapts to your evolving business requirements, user journeys, and risk profiles. Read more about Metrics and Policies to understand how
Updated 3 months ago