Review suspicious user behavior
Streamline user reviews and safeguard your platform with an automated system for flagging and assessing suspicious transactions, ensuring a balance between security and user experience.
Balancing user friction and fraud prevention is challenging. Implementing a review mechanism for suspicious behavior can ease the burden, allowing legitimate users to proceed with their actions while your support team reviews the flagged cases.
In this example, we'll use Lists to set up a simple review flow, where suspicious users are first added to a review list based on their transactions. An analyst will review the user and move them to either the trusted users list or the blocked users list, depending on the decision.
What you will learn from this tutorial
- How to set up a simple user review flow?
- How to create lists and manage entries in them?
- How to create policies that add users to a review list?
Before you start
- Ensure you have access to your Castle account with admin privileges.
- Ensure you send events you want to track (in this tutorial: transaction events).
Prepare a simple review flow
In this tutorial, you will create a flow for monitoring suspicious transactions. Any transaction over $500 and an Abuse Score over 60 will automatically trigger a manual review of the user.
Step 1: Create review list
-
Go to the Lists management page.
-
Click the Create List button in the top right corner of the page.
-
Fill in the list details:
- Name: "Users in review"
- Description: "Users that had high Abuse Score for transactions over $500"
- Primary Field:
User ID
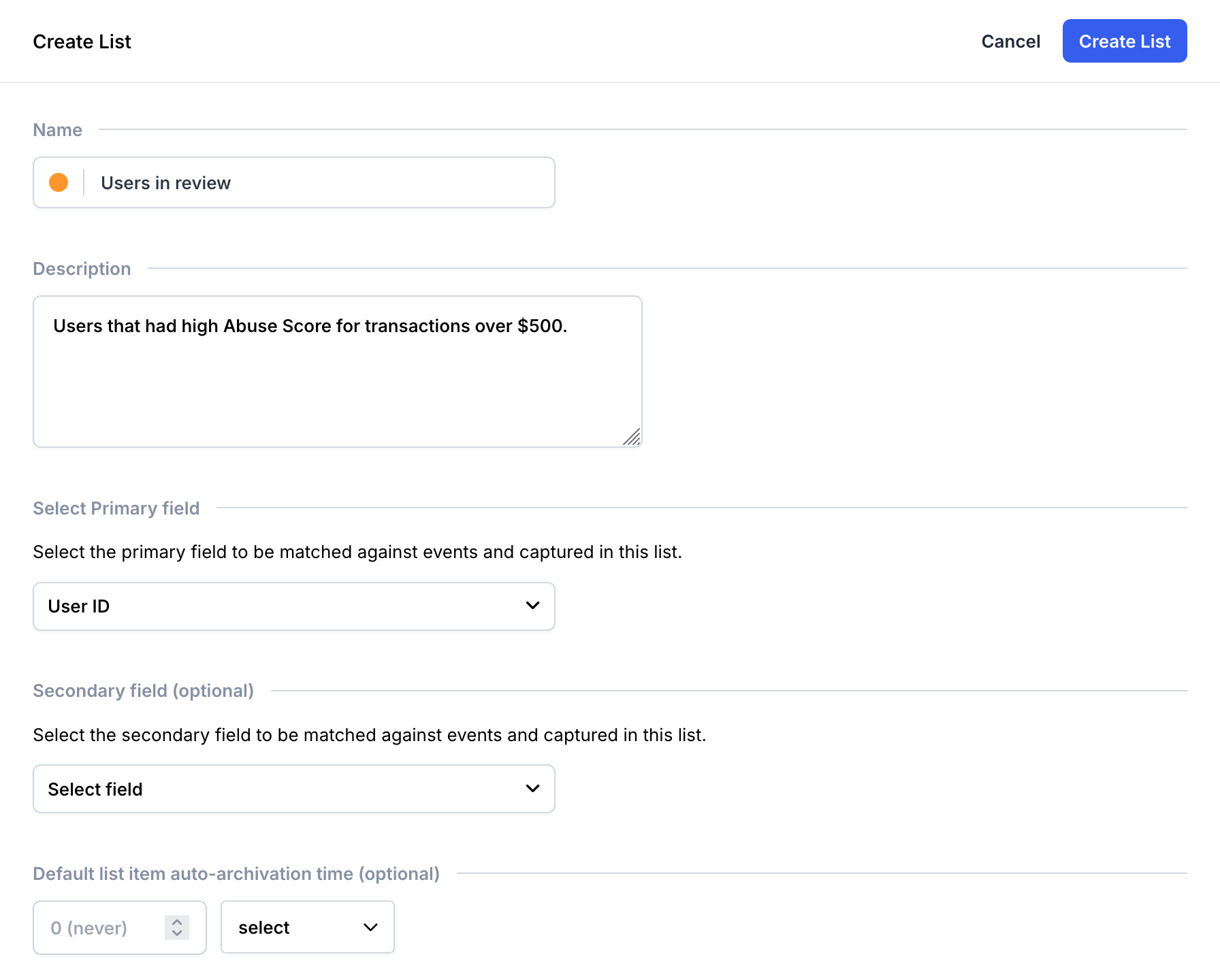
Create list form for "Users in review" list
-
Save the list by clicking the Create List button.
Missing Trusted Users or Blocked users lists?We assumed that you already have these lists as they are part of the default account setup. If not, create them according to these specifications:
- Trusted Users
- Primary Field: User ID
- Secondary Field: Device Fingerprint as Secondary Field
- Auto-archivation time: 14 days
- Blocked Users
- Primary Field: User ID
Step 2: Create a policy for catching suspicious transactions
-
Go to the Policies view.
-
Click the Create new policy button in the top right corner of the page.
-
Fill in the new policy details:
- Name: "Review suspicious high-value transactions"
- Inline action: Enable pass through
- Filters:
Account Abuse Score > 60andTransaction Amount is greater than 500 - Add to lists: Users in review
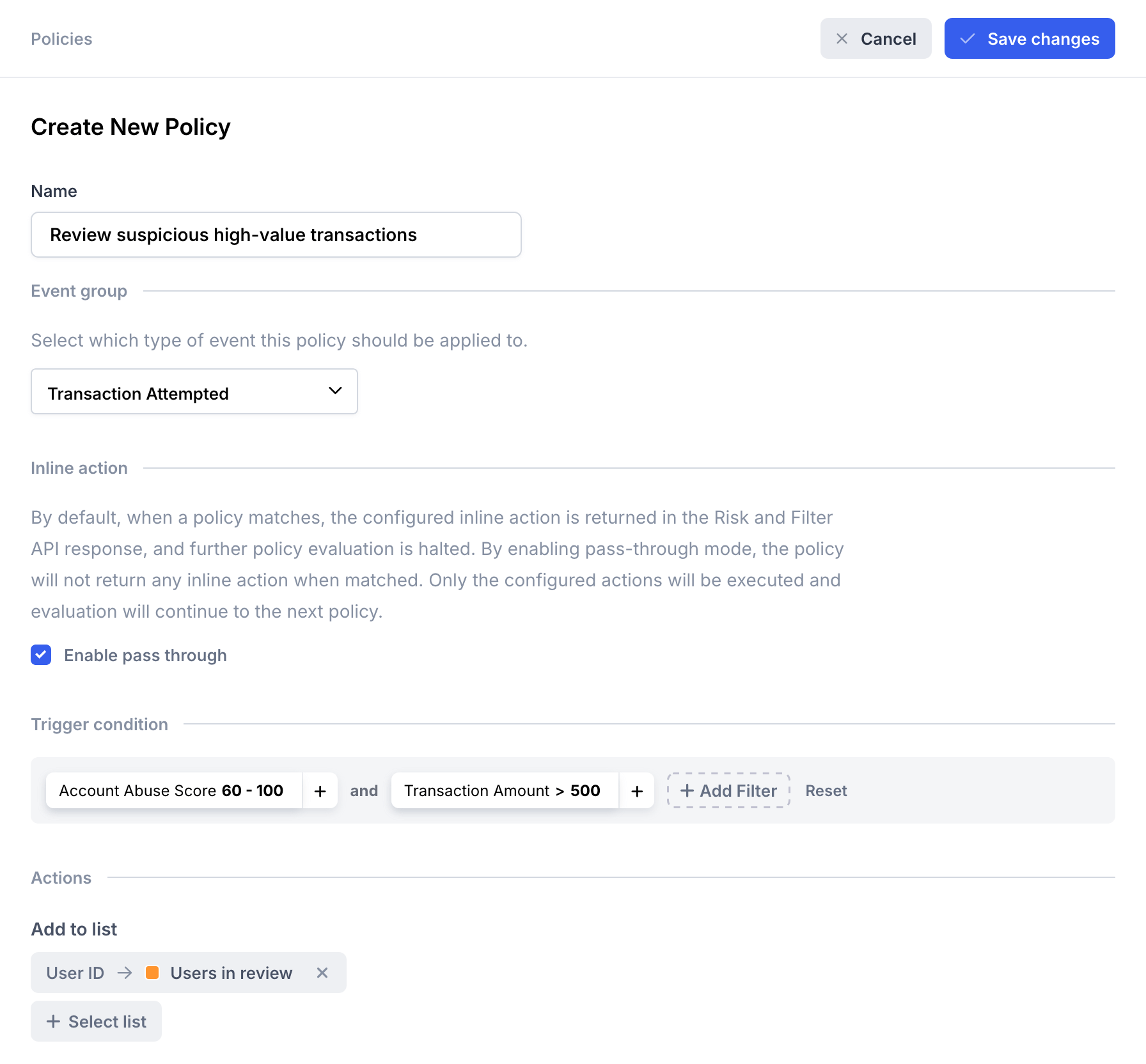
Create policy form for Review suspicious high-value transactions policy
-
Save the new policy by clicking the Save changes button.
-
Click Reorder near the Transaction Attempted header.
-
Move your policy to the top, click Save, and enable your policy.
Step 3: Your daily review flow
With the list and policy in place, users will start appearing on the list as suspicious transactions occur. A daily review flow will look something like this:
-
Open the Users in review list.
-
Select the user you want to investigate, then click the User ID and then View User button:
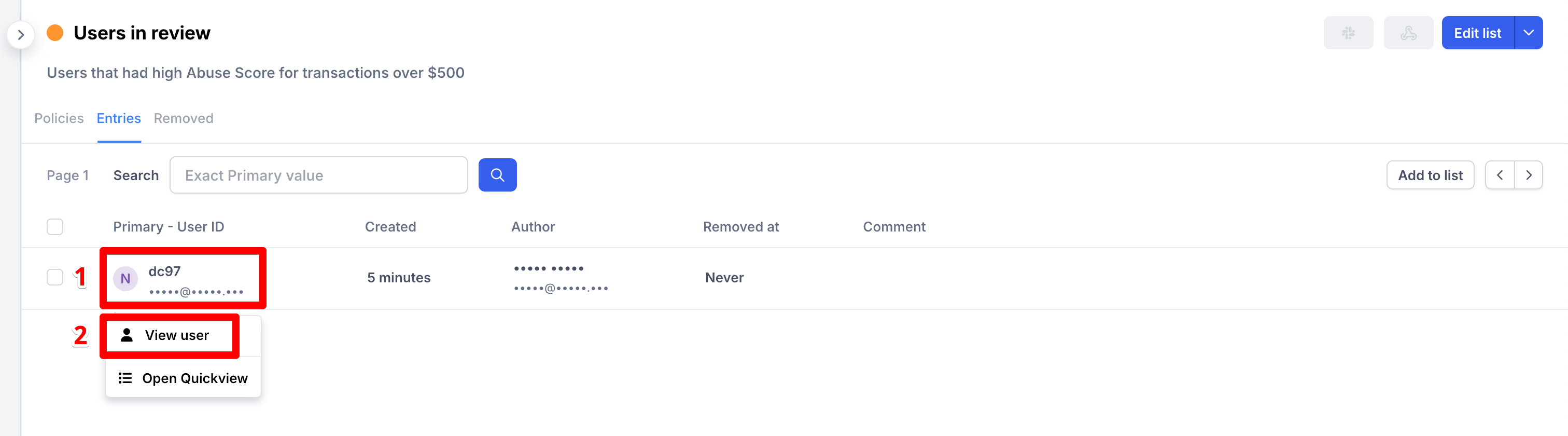
Users in review list - open the User Profile view
-
In the top right corner, click the lists button, select the three dots beside the Users in review list, and then click the Remove from list button:
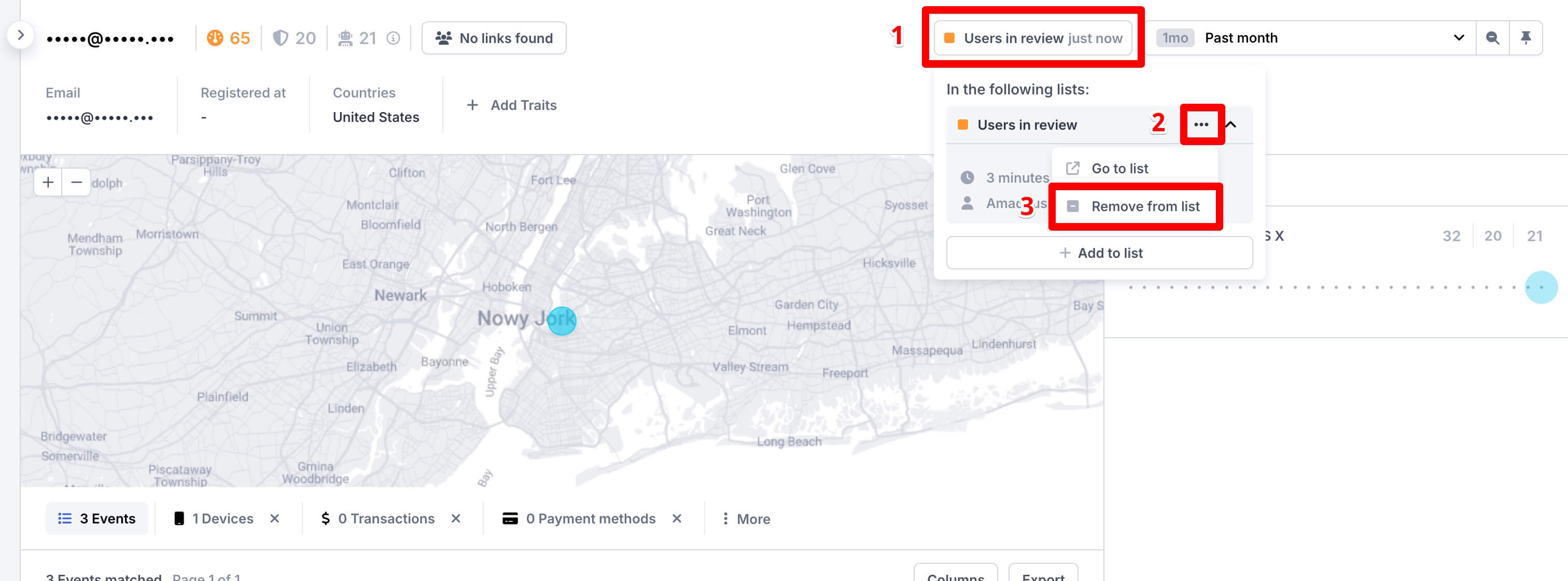
User Profile view - remove user from the Users in review list
-
Review the user activity and then, based on your decision, add the user to the Trusted Users list or the Blocked users list by pressing the lists button in the top right corner:
User Profile view - add user to the Trusted Users or Blocked users list
Make sure to enter a comment to inform your teammates about the basis for your decision. This will help them understand your reasoning when the user is investigated for different reasons.
-
Head back to the Users in review list and repeat the process.
Updated 2 months ago