Device fingerprinting
Castle offers an accurate device fingerprinting solution through a combination of client and server-side technologies, providing much greater identification accuracy compared to cookie-based or purely client-side fingerprinting techniques. Device fingerprinting works by tracking device data and per-user profile information, such as historic devices and locations, increasing accuracy.
One of Castle's unique features is that it's completely invisible to both attackers and privacy plugins, making it impossible to detect and block.
Accurate device fingerprinting is a foundation for dealing with many types of fraudulent activities, such as:
- Multi-accounting: The same individual signing up from the same device to exploit free trials or referral bonuses.
- Account sharing: Multiple individuals sharing the same account to avoid extra seat payments.
- Account takeover: Unauthorized access from new mobile devices or computers using stolen credentials, a key vector in online fraud.
Device Fingerprinting Optimized for Account Scenarios
Our fingerprinting technique is specifically fine-tuned for account abuse scenarios. While accuracy is vital for anonymous traffic assessment, reducing collisions is of utmost importance for account security. This guarantees that genuine users aren't mistakenly locked out and that alerts for any security breaches are sent to the rightful user.
- Up to 99.5% accuracy
- Ultra-low 0.0001% collision rate
Data Collection
Castle collects device attributes through its SDKs for web and mobile device fingerprinting (available for iOS, Android, React Native, and Flutter), creating a unique device ID. This device fingerprint tracker helps identify devices and monitor interactions, improving user experience and enabling seamless identity verification.
Below is an overview of some of the collected parameters based on SDK:
Javascript SDK | iOS SDK | Android SDK |
|---|---|---|
Time zone information | Unique device identifier | Unique device identifier |
User Agent | Memory information | Memory information |
Operating system | Storage, used and available | Storage, used and available |
CPU information | Location (if permission) | Location (if permission) |
System languages | Screen resolution | Screen resolution |
Mouse and keyboard interactions | Device orientation | Device orientation |
Screen size | Carrier information | Carrier information |
Installed plugins | CPU Information | CPU Information |
Canvas fingerprinting | Emulation detection | Emulation detection |
WebGL information | Jailbreak status | Root status |
Headless browser checks | Timezone information | Timezone information |
Incognito mode | System and keyboard languages | System and keyboard languages |
Tor browser | Battery information | Battery information |
Browser type | Sensor data | Sensor data |
Browser version | Device name | |
IP address |
AvailabilityMost of the parameters above are available:
- When exploring data by filtering and visualizing
- When creating Policies and Metrics
- To add to allow/deny Lists
Castle's Device Fingerprint Cannot Be Blocked
Unlike most device fingerprinting solutions that rely on outgoing API requests from client-side SDKs (which often get blocked by adblockers or privacy plugins), Castle.js employs proprietary obfuscation and randomization techniques. This unique approach allows Castle to operate without direct API requests, resulting in higher accuracy and evasion from detection by attackers. Castle’s device fingerprinting is designed to stay under the radar, significantly improving accuracy and reliability for businesses.
Device Uniqueness and Recognition
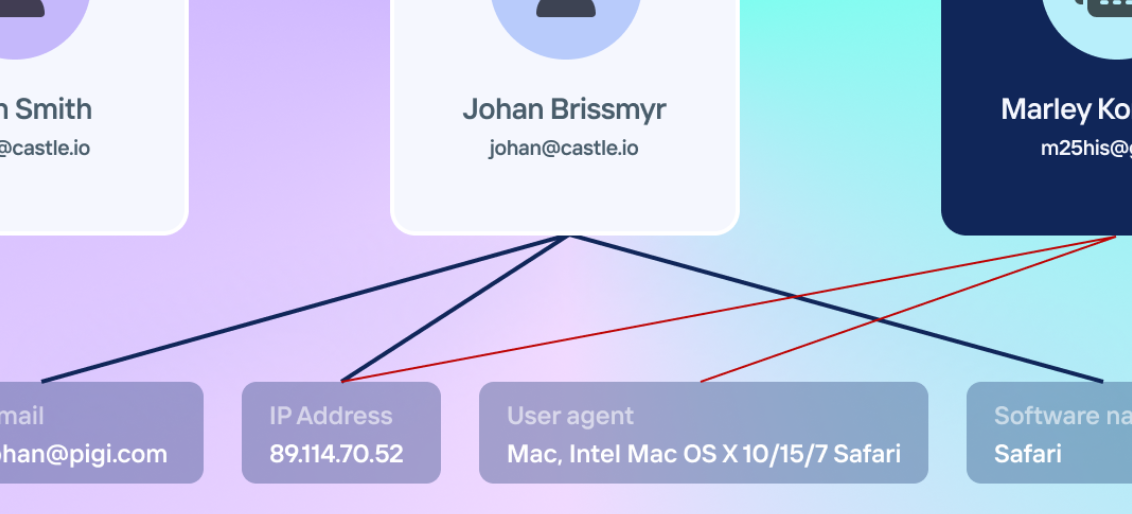
When generating a device fingerprint, Castle aims to minimize the risk of "collisions," ensuring that two different physical devices are not mistakenly merged into a single digital fingerprint. Our fingerprinting techniques are optimized to prioritize accuracy, so we sometimes prefer missing a fingerprint rather than incorrectly merging two separate devices. This design allows your team to confidently block or contact individuals seen using multiple accounts on the same device without risking false positives that could lead to customer dissatisfaction.
For example, if two users buy the same model of computer and both install Google Chrome simultaneously, even though their device configurations may be nearly identical, Castle’s device fingerprinting takes into account additional data points such as the time, context, and location of new user account creation. This ensures that each user is recognized as having a distinct unique device ID, supporting accurate fraud detection without merging separate devices.
Handling Changes in Device Fingerprint
Despite actions like clearing cookies or opening incognito mode in a web browser, Castle’s device fingerprinting will attempt to maintain the same device fingerprint for consistent identification. On mobile devices, the device fingerprints are designed to persist through app uninstalls and memory wipes. However, there are scenarios where we may prefer to generate a new unique identifier instead of resolving the previous one.
For instance, if a device fingerprint hasn't been detected for an extended period (such as over a month) and the user resets their storage or updates to a new version of the device, Castle may assign a new device fingerprint when they create a new account. Nevertheless, as long as the user logs back into the same account that they previously used, Castle will likely resolve it to the same unique device ID, ensuring consistent user identification and fraud prevention.
Detecting Device Tampering
Castle’s advanced fraud detection techniques uses machine learning to verify the authenticity of the OS claimed by the user’s user agent. While parsing the user agent and HTTP headers provides basic OS information, Castle utilizes deeper device fingerprinting techniques to detect discrepancies. For instance, fraudsters may use tools to falsify the OS displayed in their user agent. Castle’s solution cross-references multiple data points, including WebGL attributes, screen resolution, and GPU information to detect if a user’s OS has been spoofed. In addition, GPU-related attributes can reveal the actual hardware being used, and canvas fingerprinting challenges like emoji rendering can expose discrepancies in the OS. If the reported OS in the user agent conflicts with these signals, Castle flags the device as potentially using spoofing techniques and adjusts its risk profile accordingly.
Detecting Bots and Headless Browsers
Castle’s device fingerprinting solution also excels at detecting bots and headless browsers by performing a deep analysis of user interactions. By examining mouse movements, keyboard interactions, and other device attributes, Castle can differentiate between human and automated bot behaviors. Additionally, Castle scans browsers for headless signatures or the presence of privacy plugins, further enhancing its ability to detect fraudulent activities.
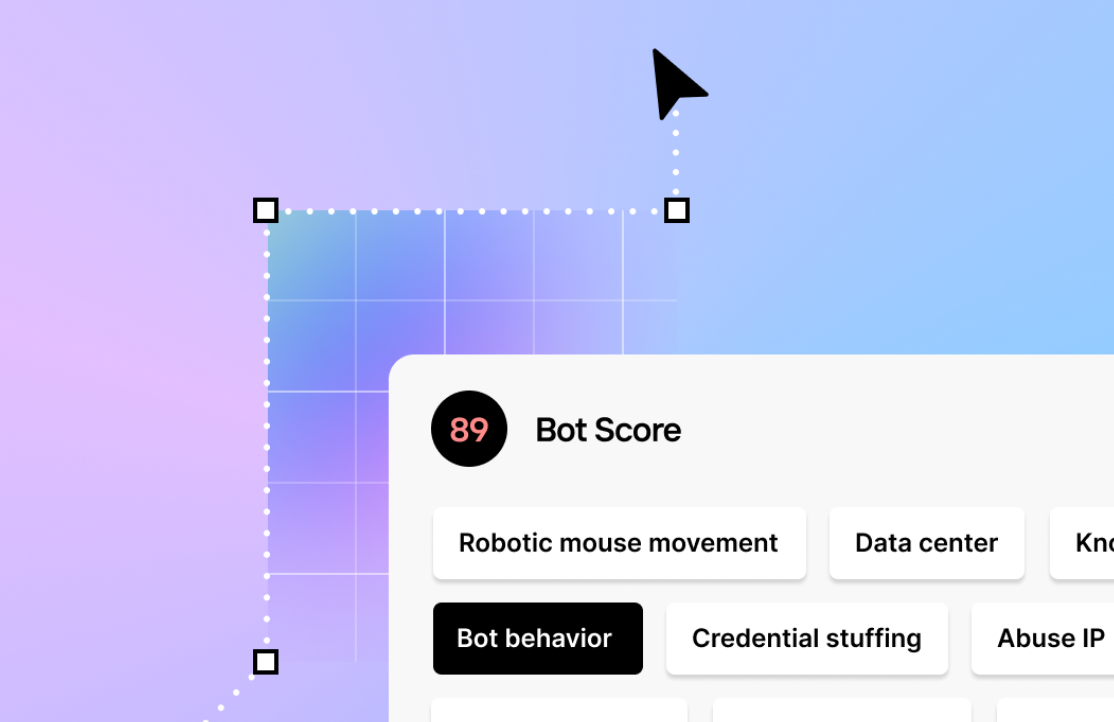
Castle provides a bot score ranging from 0 to 100, allowing businesses to evaluate the likelihood of bot behavior in real-time. This bot detection process includes:
- Analysis of mouse and keyboard interactions to differentiate between organic human inputs and automated actions.
- Detection of repetitive navigation patterns, often associated with bots.
- Identification of headless browser usage, which is commonly employed by attackers for automated fraud attempts.
- Recognition of privacy plugins or headless signatures that may indicate attempts to mask bot behavior.
By combining these automation tools with Castle’s broader device intelligence, businesses can better protect themselves from fraudulent activities such as automated signups, credential stuffing, and credit card testing.
Cookies and Storage
Castle’s fingerprinting protection employs web cookies and local storage to improve the accuracy of the device fingerprinting process. These tracking cookies are set as first-party cookies on the website owner's domain where Castle.js is deployed. They contain no sensitive information and help create a unique identifier for devices. While disabling cookies may in some cases lower accuracy, the machine learning process process works to produce a an accurate device fingerprint even when cookies are cleared. During the configuration of Castle.js, there is the possibility to disable the use of cookies as well as setting the cookie domain explicitly.
Supported Platforms
Fingerprinting is available for the browser (Castle.js) and for various mobile application development platforms, including native iOS, native Android, React Native, and Flutter.
Castle’s device fingerprinting solution supports web browsers via Castle.js and mobile devices through SDKs for iOS, Android, React Native, and Flutter.
How Device Fingerprinting is Used
Account Takeover Protection
Castle’s device fingerprinting helps prevent account takeovers by leveraging device recognition and historical data to reduce the need for constant 2FA without compromising account security. When a user logs in, a device fingerprint is generated and associated with their account. Instead of requiring 2FA for every login, Castle tracks the number of distinct fingerprints tied to that account. If a new device fingerprint is too anomalous compared to other devices on that same account, Castle flags the event as suspicious and produces a high ATO score. Additional security measures like identity verification can then be triggered, ensuring fraud protection while minimizing friction for legitimate users.
Multi-Account Fraud Prevention
Multi-accounting occurs when users create multiple accounts to exploit free trials or referral bonuses. Castle’s device fingerprinting solution helps detect this behavior by analyzing device data and checking how many accounts are associated with a given device fingerprint. If the number of associated accounts is below the set threshold (e.g., fewer than 3), account creation continues as normal. If the number is higher, Castle can trigger friction points, such as requiring additional identity verification via phone validation. This flexible approach balances fraud prevention with a seamless user experience for legitimate users.
Account Sharing Detection
Castle’s device fingerprinting also helps identify account sharing by monitoring the number of distinct fingerprints accessing the same account. If an unusually high number of devices (e.g., more than 10) are logging in from varied locations or device types, Castle flags the account for further inspection. This ensures fraud detection and user tracking without continually interrupting legitimate user behavior, while providing a safeguard against abusive sharing. Accounts flagged for account sharing can then undergo additional checks or identity verification.
Security and Privacy
At Castle, we design our device fingerprinting solutions to create secure and seamless digital environments, protecting against fraud and abuse while prioritizing user privacy.
Each unique identifier generated by Castle is site-specific. Even if a user visits multiple sites that use Castle, they will receive different visitor identifiers, preventing cross-site tracking. Castle prioritizes same-site tracking to help businesses secure their platforms while maintaining user trust. Our device fingerprinting and fraud detection technology is optimized for industries such as finance, gaming, SaaS, and e-commerce. Castle works well for same-site tracking and personalization but is not designed for cross-site tracking or targeted advertising. Therefore, Castle should not be used for personalized advertising purposes, ensuring a privacy-first approach.
Castle’s SDKs, whether for web or mobile, require no additional browser permissions. This zero-permission policy ensures smooth integration into your application, with no intrusive permission requests to users, keeping the user experience uninterrupted.
Castle makes it nearly impossible for attackers to impersonate a device fingerprint. Our tracking technology detects discrepancies, making it safe to compare fingerprints and trigger additional security measures when necessary.
The fingerprinting data is represented by a variable called request token which is designed to be generated fresh before each server-side request to Castle's APIs. Tokens are meant to be used only once per server-side request and will expire after 120 seconds. If a request token generated for a specific device is copied and used for a different device, we apply spoof detection in order to detect such tampering.
Open Source
Castle's mobile SDKs are open-source repositories on Castle's GitHub account. We welcome the creation of issues and pull requests from the community
Updated 2 months ago