Detect account sharing
Prevent revenue loss due to abusive sharing of a single account
Account sharing, or credential sharing is when multiple individuals are using the same set of credentials to access your service. It is a common problem in particular for services that charges a fee per seat or per account, such as online streaming services or B2B software. For these services, account sharing leads to revenue loss, so it's important to stay on top of this and to put mechanisms in place to either prevent this entirely or inform the affected accounts about their abuse.
In this guide we'll use Metrics and Policies features in Castle to set up an account sharing detector, for which you'll be able to tune the thresholds based on your actual data.
The expected behavior of accounts that are being shared is to see overlapping activity from multiple devices and (potentially) multiple locations.
Improving detectionThe more events you track to Castle, the easier it becomes to detect account sharing, just because there is a higher likelihood of observing overlapping activity between devices. On the flip side, if you eg. only track login events, and have long lived sessions, it becomes hard to catch account sharing in the act.
How to set up account sharing detection in Castle
Step 1. Create account sharing metrics
First we need to set up a metric that we'll use to detect account sharing.
-
Log into your Castle account
-
Go to Metrics page (on the left-hand side navigation, at the bottom) and then click "Create metric" button in the top right corner of the page
-
Set up your account sharing metrics:
-
Number of unique devices per account, within a one-hour interval:
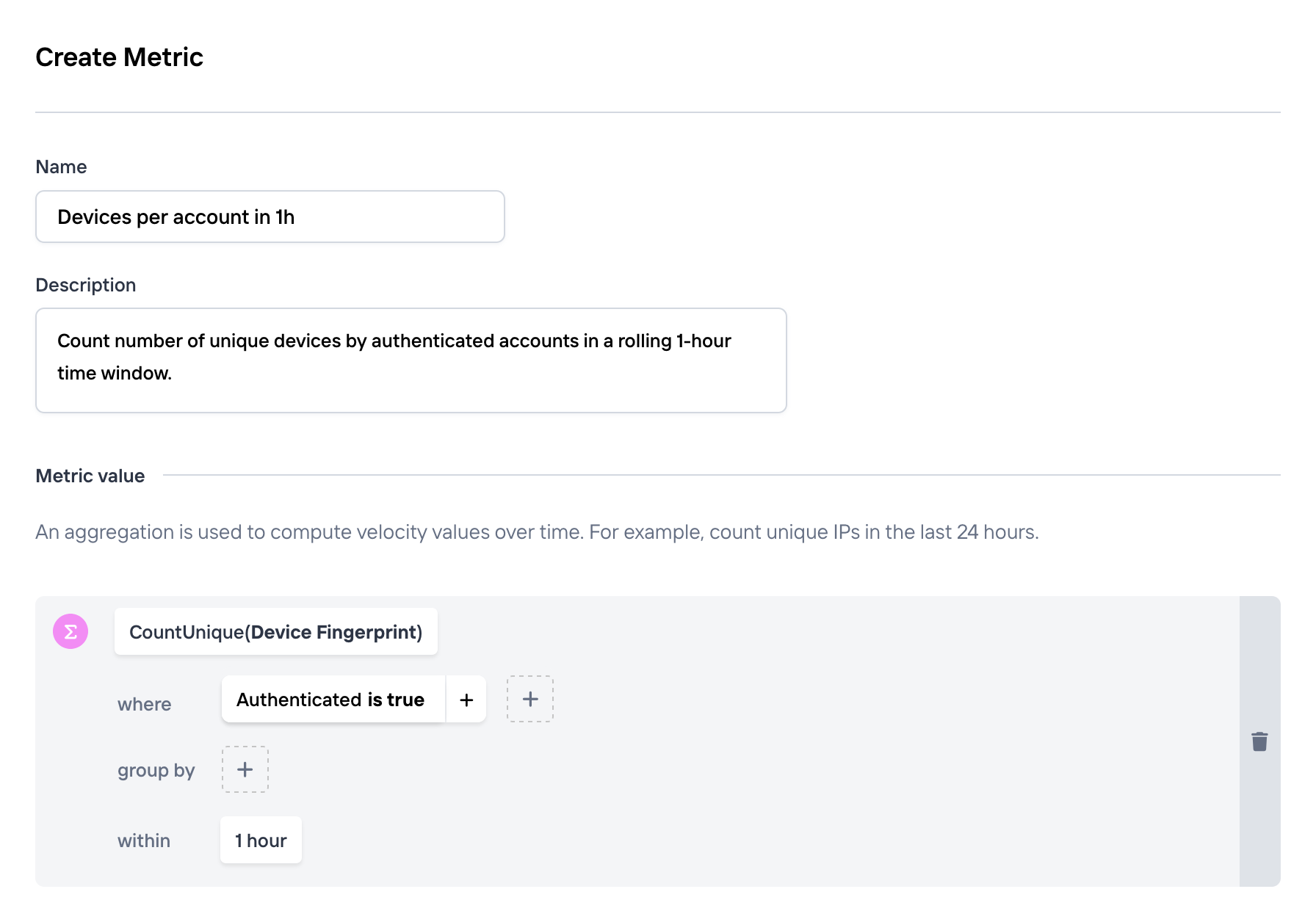
-
(optionally) Number of unique IP addresses per account, within a one-hour interval:
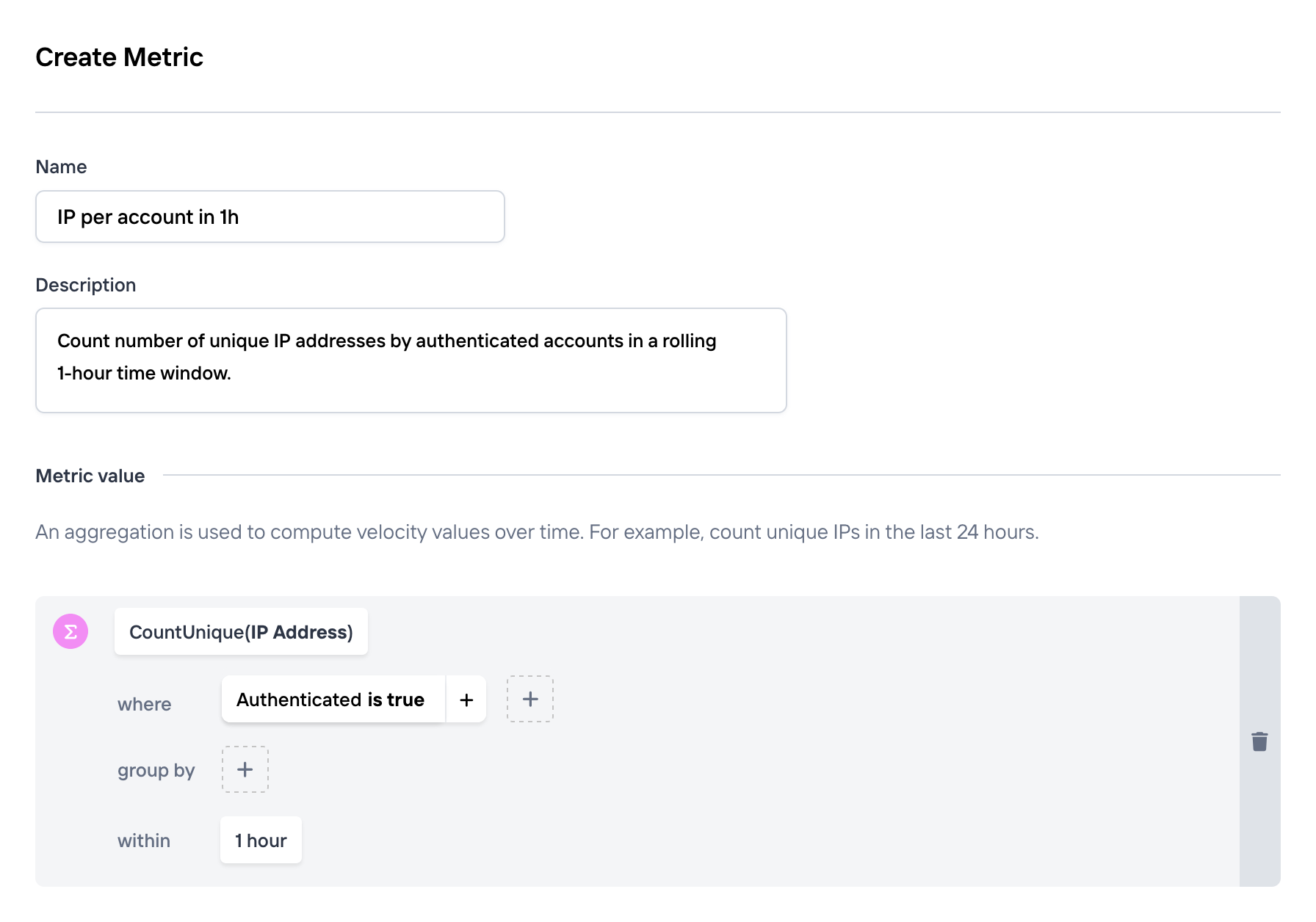
-
Adjusting metrics to your needsIn Castle we give you the power to adjust behavior to your business needs. In case of account sharing you can decide on:
- How big your time window is: a shorter one will allow users to switch devices more often (i.e switching from watching a show on a phone to watching a movie on TV), a longer one will catch more cases in a long-lived user sessions (i.e. users log in once every 14 days and rather uses your service on a single device)
- How you define a single location, i.e. the same city (a rather relaxed option), the same postal code, or even the same IP address (a strict option)
- If you allow to simultaneously use a mobile device and a desktop/laptop
Step 2. Create account sharing policy
Next step is to set up a policy that will help you act you when account sharing is detected.
-
Go to Policies page (on the left-hand side navigation, at the bottom) and then click "Create policy" button in the top right corner of the page
-
Set up your account sharing policy
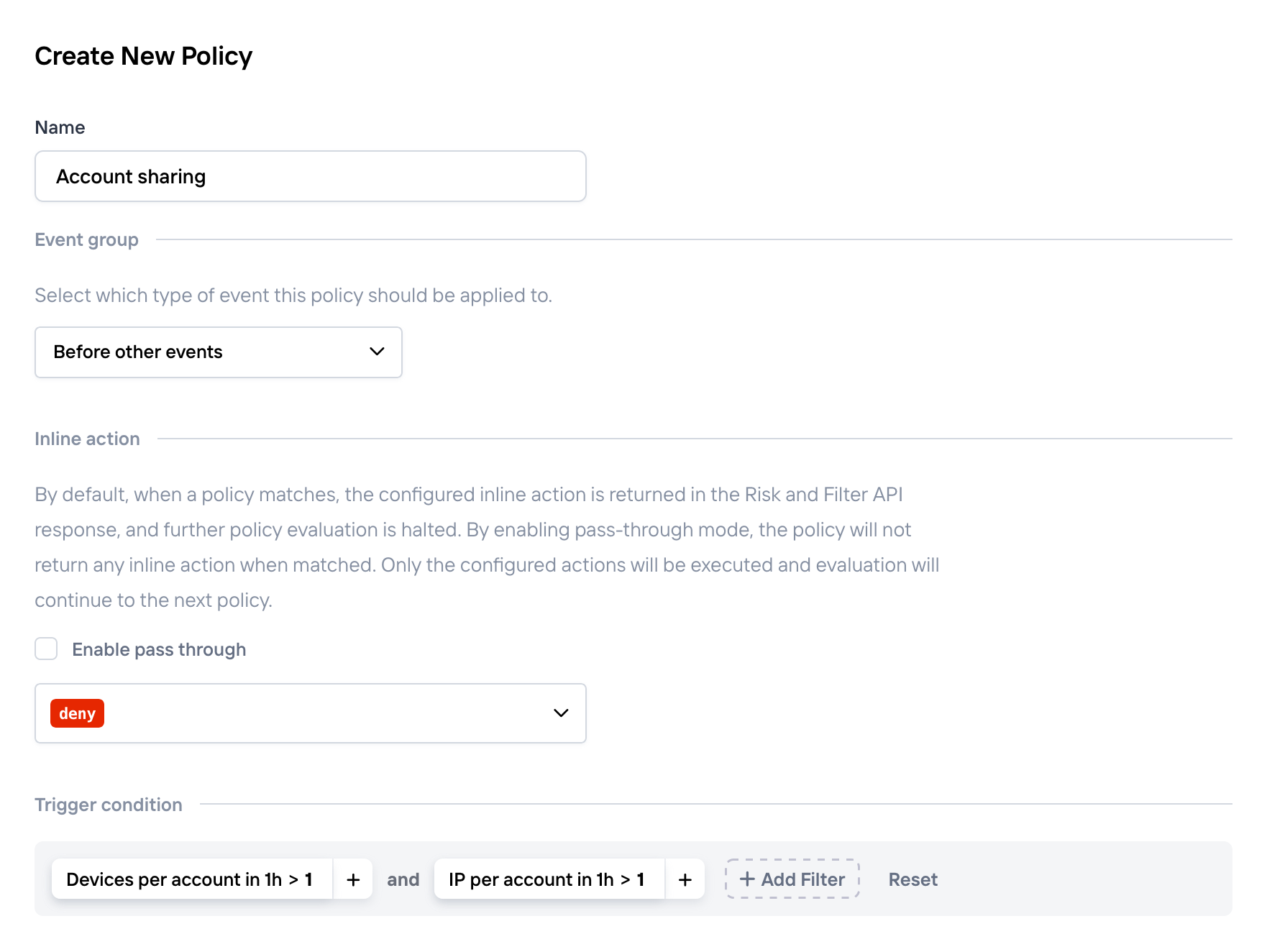
Adjusting your policy to your needsThe recommended policy is strict and so you might want to tune it a bit:
- Allow more than just 1 device
- Skip IP check or allow more than just 1 IP
- Challenge the user instead of denying access (advanced)
- Run the policy only on a certain event (i.e. only on Login Succeeded)
- Don't block the access, but add the offending users to a review list so that you can review these manually and reach out to the offenders
- Subscribe to the List webhooks, to automatically notify and suspend the account, when multi accounting is detected
Step 3. Act on Castle's inline action
Last step requires some changes in your app's code: you need to check the policy.action field in a response from a call to the Castle's Risk API. It is needed to understand what your policies result is and what your app should do now.
For example: you can deny login requests when account sharing is detected, and pair this with automated messaging. For users that systematically abuse your service this might impose enough friction and annoyance to make them reconsider purchasing separate seats.
Step 4. Test your policy and enable it
New policies in Castle are disabled by default as they might influence your app behavior. We recommend that you test the policy within our Exploring data view before enabling it:
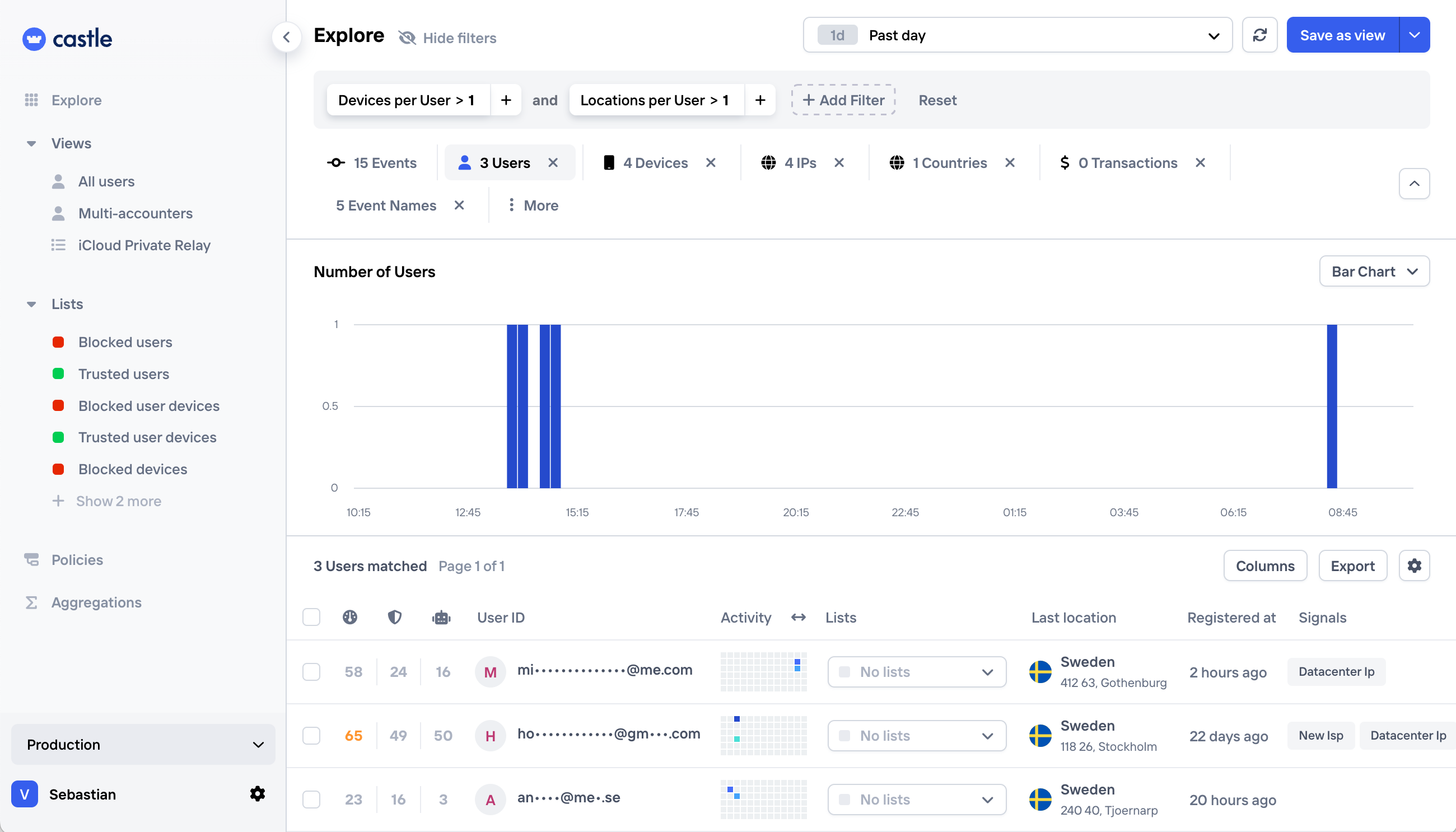
To enable the policy just open the Policies view and toggle the enable switch:
Tuning the policy thresholds
For the most aggressive detection, filter for events where Device per account in 1h > 1 OR IP per account in 1h > 1. However, with this setting you may end up catching users switching from their mobile phone to their computer, or vice versa. If you'd switch the OR operator to an AND you'd allow this case, as long as the user is on the same Wi-Fi or connection.
If your intention is to only catch severe account sharing, you may instead set a higher threshold for Devices per account in 1h, such as > 3
Test your policies before applying changesEach change to policies can affect your customers. To avoid disrupting them we recommend that you test your policy changes before acting upon it within our Exploring data view.
Updated 2 months ago
With account sharing detection you can prevent excessive revenue loss. Learn even more how Castle can help you protect your customers and your business.