Handling Device Reporting with Lists
Report and block suspicious devices to prevent them from accessing legitimate user accounts on your platform.
Ensuring that only authorized devices access your platform is crucial for protecting your users' accounts. Implementing a system to report and block suspicious devices is necessary to achieve this protection.
In this tutorial, we'll set up a device reporting flow using lists and policies. Suspicious devices can be added to a list either manually or through a policy. Once on the list, these devices will be blocked from performing any actions on your platform (like login, registration, transaction..).
What you will learn from this tutorial
- How to set up a device reporting flow
- How to create lists and manage them
- How to create policies that block devices
Before you start
- Ensure you have access to your Castle account with admin privileges.
- Ensure you send events you'd like to protect to Castle.
Set up a device reporting flow
To implement a process for reporting and blocking devices, we need two key components: a list and a policy. First, we will create a Reported Devices list. Next, we will establish a policy that denies access to users based on this list.
Step 1. Create a list for reported devices
- Go to the List Management Page
- Create a new list called Reported Devices with the following details
- Description: Devices in this list will be blocked
- Primary field:
Device Fingerprint
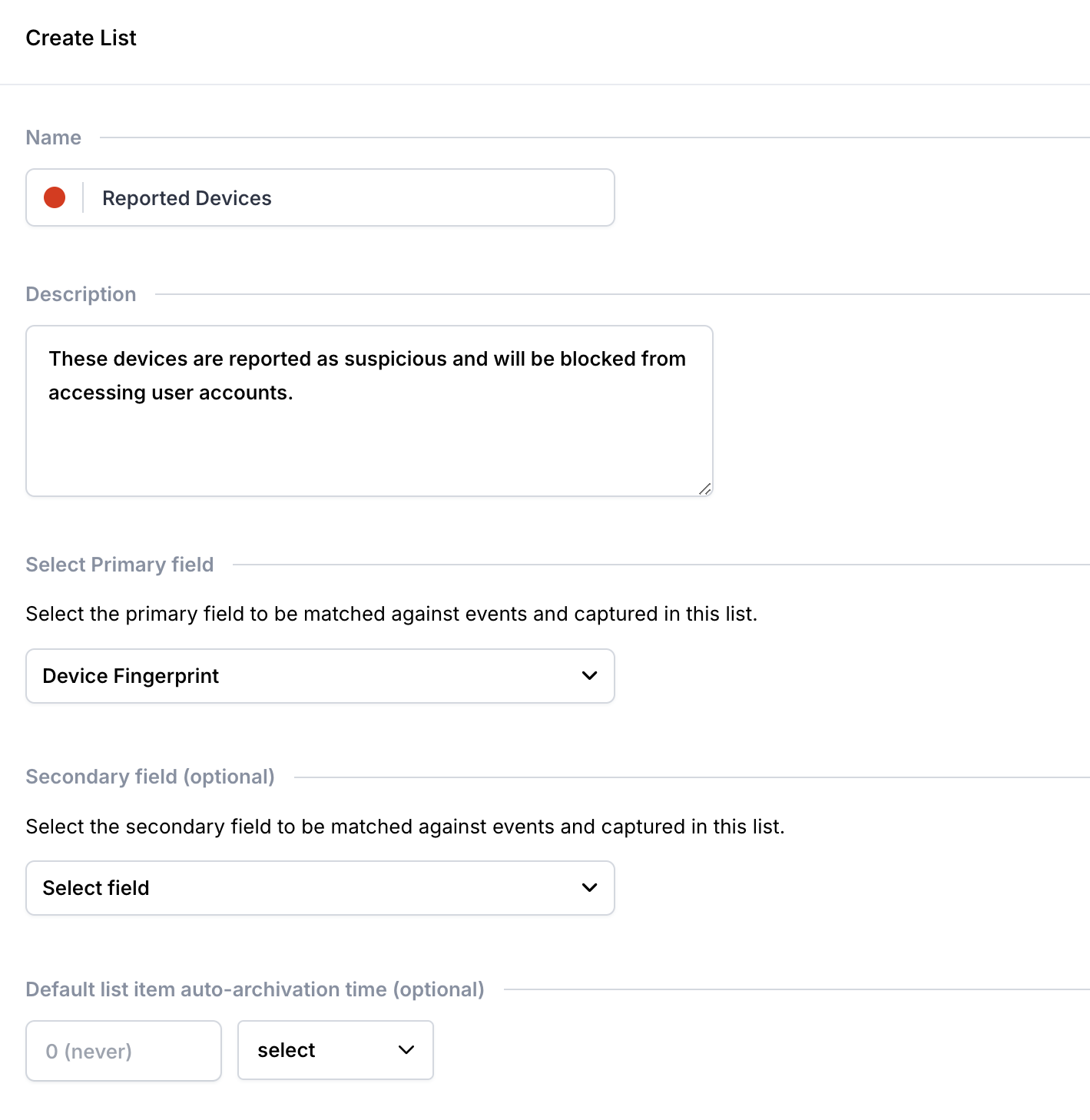
"Reported Devices" list
Step 2. Create a policy to deny on the Reported Devices list
This will ensure that anytime Castle detects a device from the list, a "Deny" action will be returned.
- Go to the Policies Page
- Create a policy named Deny Reported Devices as shown below:
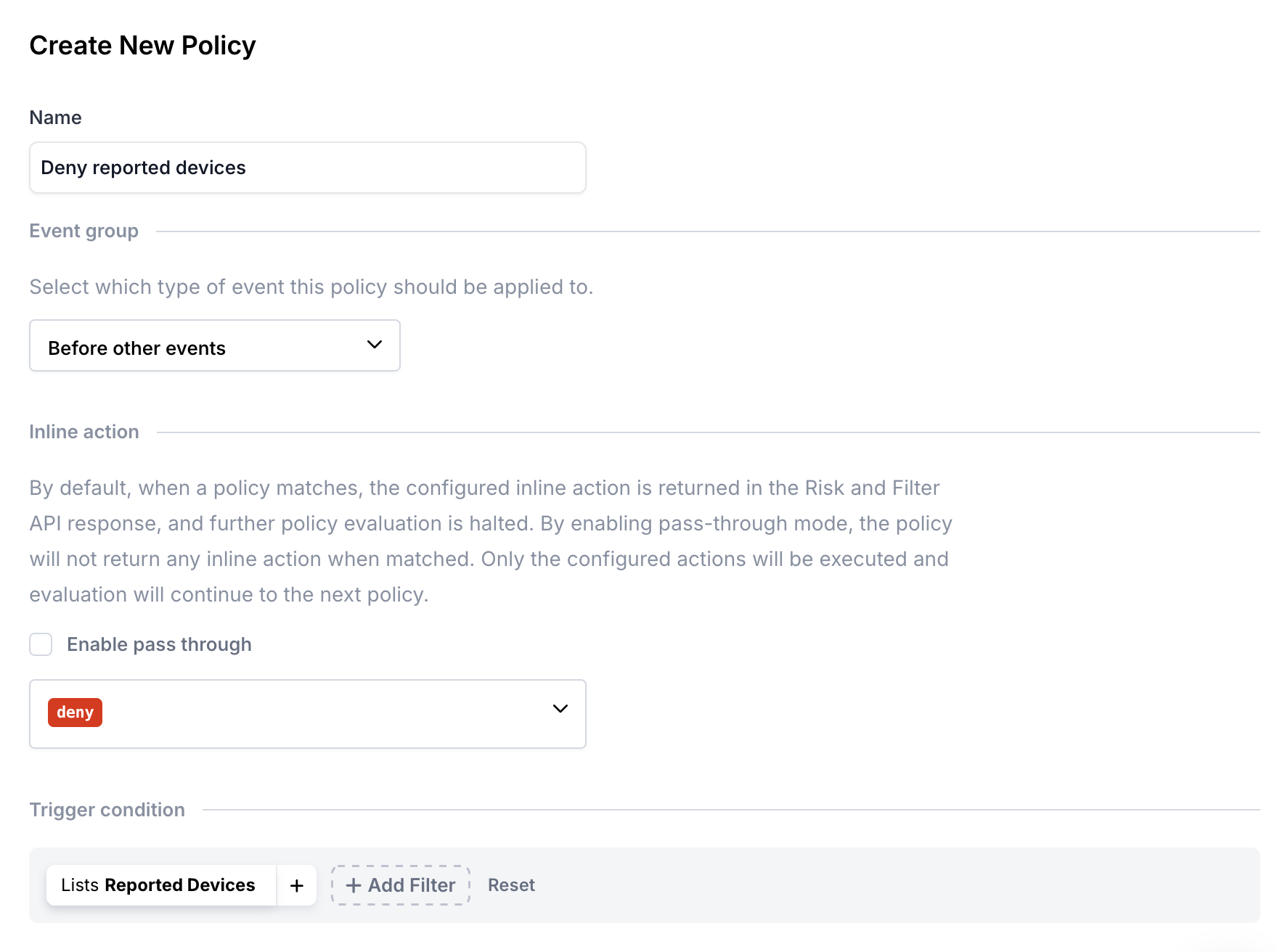
"Deny Reported Devices" Policy
Step 3. Start Adding devices to the list
Devices can be added to the list in multiple ways:
- Manually from the Explore View or the User Details views on the dashboard. See examples in our Lists Documentation.
- Automatically through policies: You can create policies to flag the devices to block. The policy details will depend on how you define bad actors within your system. Let's say you don't allow one user to have multiple accounts. We can create a policy to deny devices where more than one account is detected, and add the device fingerprints to the list we created in Step 1.
- Create a new policy named Deny multiple accounts.
- Add any detected device to the Reported Devices list.
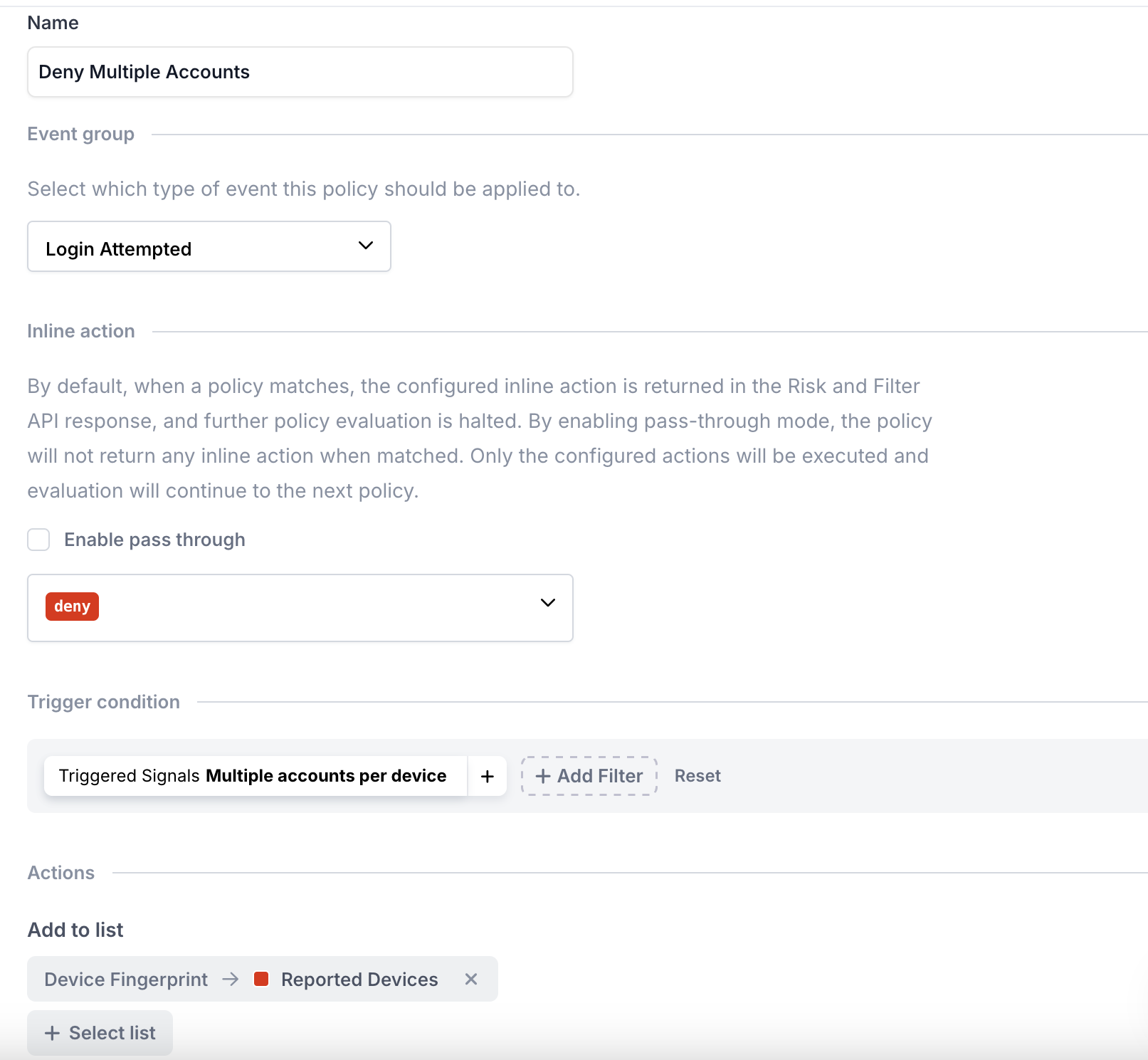
TipYou can add devices to the lists from multiple policies at a time.
[Optional] Step 4. Block user actions from your application
To effectively block actions from devices on the Reported Devices list, you should implement measures that trigger whenever a reported device attempts to interact with your platform. Here are some approaches you can take:
- In-line blocking: You can trigger your device-blocking code when you receive a "deny" action in the responses from the Risk or Filter APIs.
- Webhook Integration: Add a Webhook to this policy. When triggered, Castle will send an HTTP request to your server. Ensure your server handles this request to initiate your application’s device-blocking flow. Learn more about how to subscribe to webhooks from Castle
- Slack Integration: Implement a Slack integration to notify your team whenever a reported device is detected.
Updated 3 months ago